
Size is not a determining factor when it comes to mission-critical control centers. Video walls can comprise just a few displays receiving feeds from only a dozen cameras, to hundreds of inputs streaming on 64 displays.
As facilities scale in physical size or the scope and their monitoring needs increase, it’s essential that the control room system can scale as well.
Darin Crosby, Global VP Sales at Datapath’s Philadelphia, Pennsylvania headquarters suggests choosing a system that’s modular so that you can start small and build out based on budget and key requirements. “This allows facilities the ability to expand easily and gradually, and in a cost-effective way,” he says.
A modular system will help scale the primary security room, surrounding crisis rooms, or huddle spaces need to access and share all the same sources from a single control point without requiring extra routing switchers.
Sharing mission-critical content from a central control room to a crisis room or another secure location is a desired feature. Today content can be encoded and securely share any source to authorized users anywhere via IP. Until recently, this has required duplicate AV equipment for each room.
Faster Decision Making
The relationship between the centralized main video wall display and control room operators has been long established. Video wall content is monitored for events, and the operator analyzes the details on his/her station display to make an informed decision to escalate an event to the next level.
New collaboration software tools enable operators to isolate a particular source from the video wall, bring it to the desktop and resize windows to help them make a decision, then share the content over IP to any location on the secure network. This enables faster decision making, especially when key people are in the field. Ensuring the signal from any source can be securely encoded over IP and sent wherever is a game-changer.
This peer-to-peer networking model makes collaboration possible without the cloud. Control center communication stays behind the company firewall and allows teams to collaborate directly without any traffic through a central server.
User Rights Management
Like an enterprise network, not everyone should have full access to every area. A video wall control system should have the ability to set user rights. “For example, certain operators might be responsible for specific sources in certain zones in a casino,” says Mark Bohs, Director of Sales for the Americas at Datapath’s Philadelphia, Pennsylvania headquarters.
There are many subsets of user rights management, and the ability to set multiple levels is critical. Making sure restricted areas aren’t displayed will help ensure an operator can’t mistakenly try to view one. “Being able to separate out your sources with a security level, and then grant access to only the right people is a critical part of security,” adds Crosby.
Sharing Software
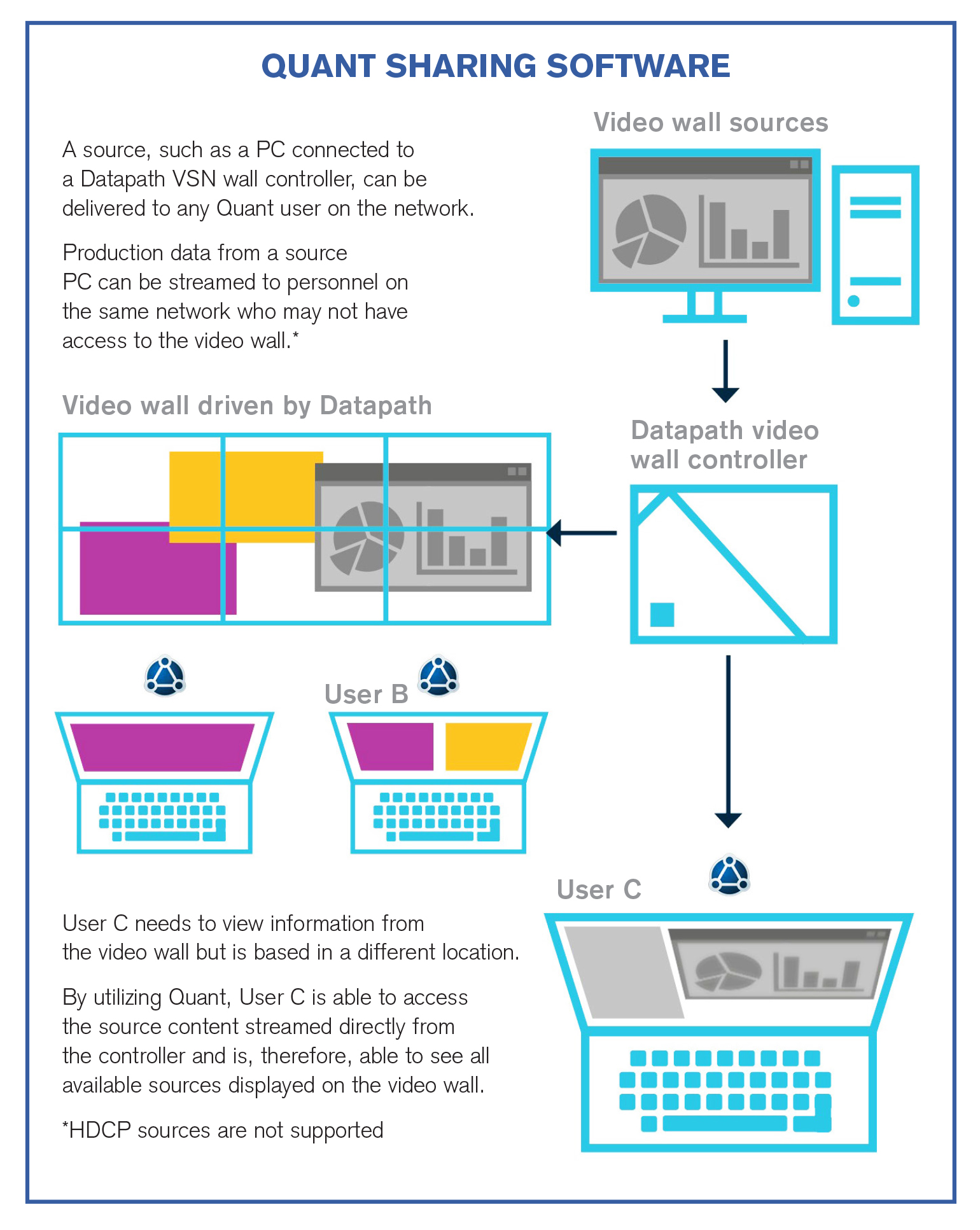
Developed to work seamlessly with Datapath wall controllers is Quant, an intuitive software that allows users to share application windows.
Operation of critical control rooms benefit from using Quant to allow the seamless sharing of information.
Physical sources connected to the controller can be streamed to any Quant user on the network, giving them up-to-the second information wherever they are. Video wall content can be accessed by users in different locations, allowing for better-informed decisions and faster response times.
Quant also enables you to share numerous application windows to both video walls, and to other peers who are able edit the application in real time.
Users have full control to decide what to share, with whom to share and what permissions are given. The interaction with shared application windows can still be made even without the file software on your own computer.
Application windows can be simply shared using a dedicated Quant icon or the drag and drop curtain. Real-time interactivity with the same application window means changes are seen as they happen.
Quant uses a peer-to-peer networking model that makes collaboration possible without the cloud. This means all communication stays behind the company firewall and allows the clients to collaborate directly, i.e. without any traffic going through a central server. The software uses TCP (Transmission Control Protocol) as the connection and data encryption protocol.

