At trade shows, I occasionally walk into a booth and discover a product I really want to understand and appreciate. I am especially interested in how the traffic it sends or receives affects the network, and how it interacts with other types of traffic. To clarify this, I often ask the engineers to tell me about the structure of the packets that are transmitted.
This is an important question because the answer usually reveals a great deal about the product and its effect on the network. It may even indicate how secure the product is. IP data packets consist of headers and data. For example, the Ethernet data frame consists of two addresses: a field that describes the data field, and the data itself. Most often, that data field is an IP packet. The IP packet, in turn, has a header and a data field. To understand Ethernet, IP, TCP, UDP, RTP and any of the hundreds of protocols used in the IP world, you need to comprehend the header that each creates.
Figure 1: IP Header Format
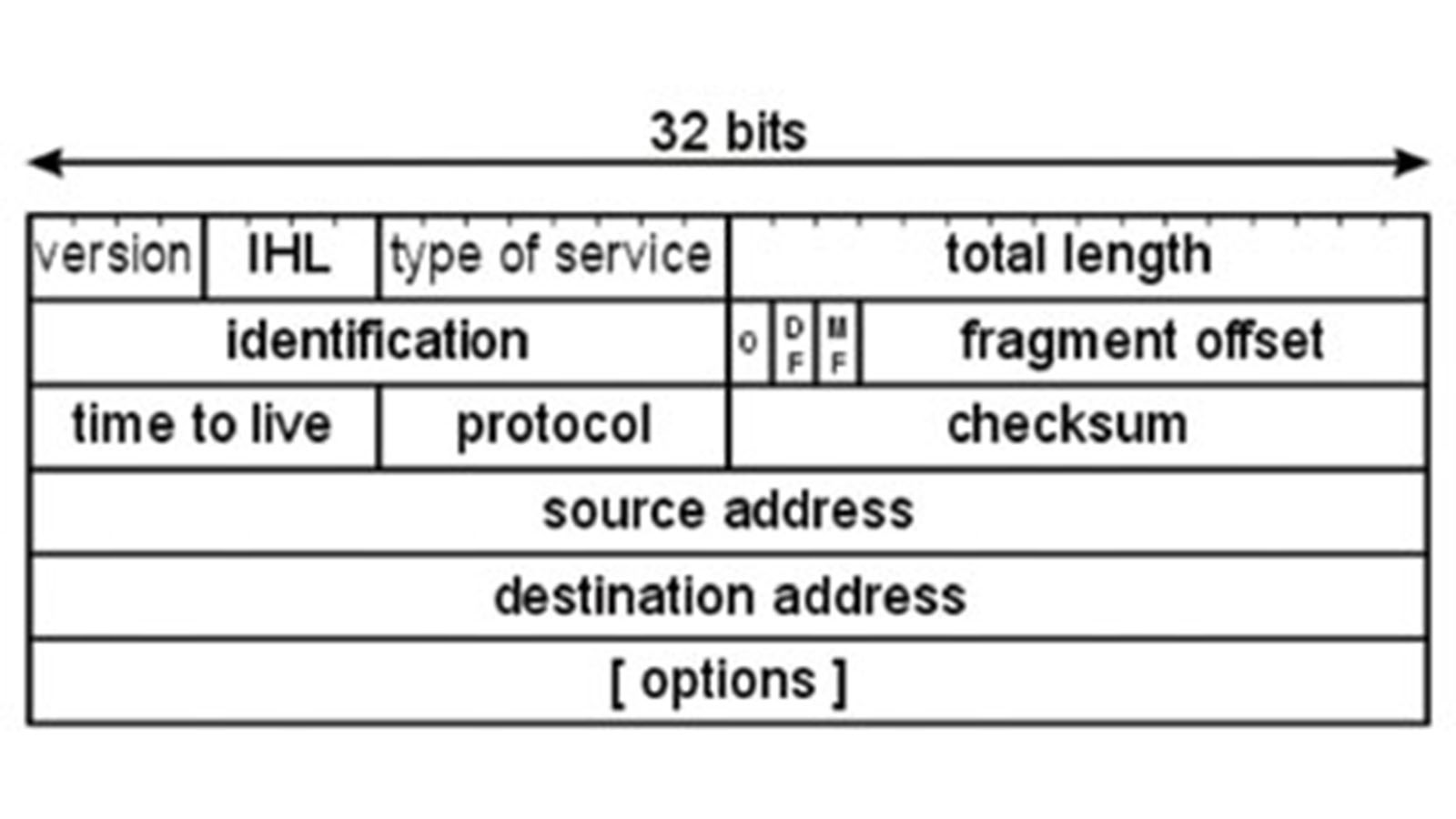
While we can’t cover all the variations in one lesson, let’s look at one example. Let’s suppose we want to understand what IP can do. Figure 1 shows the header created by the IP protocol. We find these key fields:
- Version
- IHL (internet header length)
- Type of service
- Identification, fragment offset, and a few other bits
- Time to live
- Protocol
- Checksum
- Source and destination addresses
First, note that the identification and fragment offset and nearby bits are almost never used. However, there is a lesson here. These four bytes (32 bits) are transmitted in every IP packet. This represents wasted bandwidth. Likewise, the option field rarely is included. However, it is nearly impossible to change the protocol to eliminate these fields. The version number is virtually always 4. This type of service allows for a priority code to be inserted. So, from this, we know IP can support variable levels of quality of service (QOS). The total length allows devices to know when they have read the entire data field that follows the IP header. The time to live, often called hop count, is a value that sets the maximum number of routers that the packet can pass through. This is a means to detect packets that get caught in a loop and will waste network bandwidth. The protocol is a code that describes the contents of the data field and it is always either 6 (TCP) or 17 (UDP). The checksum is an error code to protect against corruption of the header during transit. The addresses are those of the sending and receiving devices.
So, can IP support retransmissions? No, there isn’t a counter or sequence number that indicates the order or the progression of the packets. Can IP tell if the receiver is getting more data than it can process (control the flow of packets)? No, there isn’t a field that shows the size of the destination receive buffer. However, IP has all the capabilities described above. If you study another protocol, such as TCP (Transmission Control Protocol) or RTP (Real-Time Protocol), you will find that the key to its capabilities is always revealed by the header that each puts into an IP packet. This is the reason that packet structure is important.