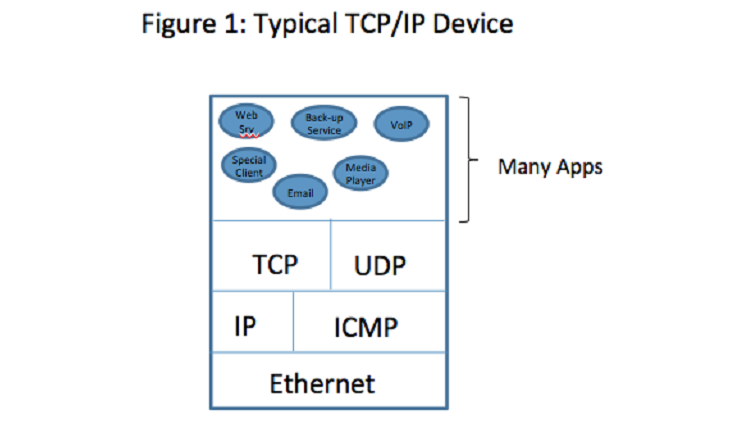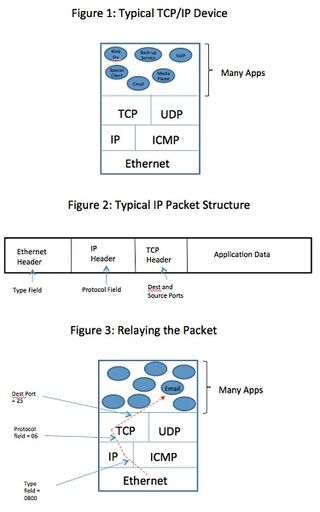
After glancing at Figure 1, does it make you wonder how a data packet makes its way from the network to the correct application that will process the data it contains? How is it that an email message is routed to your email client and not to your music player software?
The answer is explained by looking at the typical structure of a data packet. Figure 2 shows the structure of a representative packet. However, you can follow the path I’ll describe by referring to both Figure 2 and Figure 3. When the packet arrives at your NIC (network interface card), the NIC driver processes the Ethernet header if the destination mac address matches your computer. The driver reads the type field to determine what software is next in line to process the packet. In our illustration, this next process is IP, so the type field will contain the hexadecimal code 0800. After the hand-off to the IP software, IP reads the protocol field in our example and discovers the value 06. That’s the code for TCP (Transmission Control Protocol). Once again, the packet is turned over to the TCP software. The TCP software handles reads its own header and takes care of some matters related to sequencing and flow control. Then, it looks at the destination port number to determine which application will be processing the data.
As a packet is relayed from Ethernet to IP to TCP to the appropriate application, the operating system (OS) plays a critical role. At each step, the function currently processing the data must notify the OS that the data is about to be relayed by issuing an interrupt. The OS coordinates the hand-off and makes sure the data is stored in an appropriate buffer for the next process.
Understanding this process is more than just a matter of satisfying our curiosity. It can be helpful in isolating and capturing traffic destined to a particular destination. For example, suppose I have a security device configured to send an email every time a certain network condition develops. If I have Wireshark attached and tell it to capture all traffic with destination port 25, the port commonly used for this purpose, I’ll capture all the emails. This can be useful as evidence or for post-process analysis.
Phil Hippensteel, PhD, is a regular columnist with AV Technology magazine. He teaches information systems at Penn State Harrisburg.