When I’ve talked with students, relatives, and friends about computer security, they often questions such as, “Why can’t the bad guys just steal the key?” Or, “Can’t they find out what the encryption key is by listening to the conversation?” Pondering how to make the exchange between your browser and your camera secure can be daunting. Modern computer and network security is vastly different from the era when Allen Turing and the secret team at Bletchley Park defeated the German Enigma machine. For one thing, the encryption keys in that World War II setting were used across and entire army for a day or more. Today, when a key is created for a communication session, it is used for that session only. In fact, more often than not, the key is changed many times during one session. In addition, Turing’s group needed to find a key from among many billions of possibilities. Now, the number of possible keys that must be guessed could be in the trillions of trillions of trillions or more.
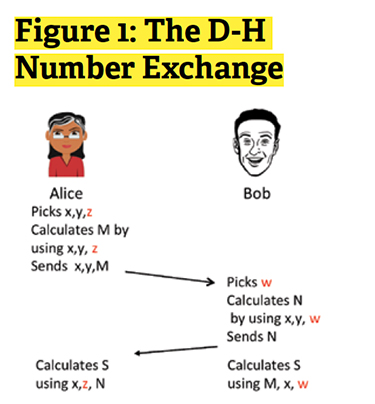
There are some situations where keys can be discovered by brute force (repetitive guessing) and we should be aware of these. For example, when pre-shared keys are used in Wi-Fi, an eavesdropper can use tools available on the Internet to try every possible combination of potential keys. By artificially generating enough traffic to see many millions of responses from an access point, the attacker can often guess the phrase that generated the key. However, the most widely based form of encryption is based on the technique used in the SSL (Secure Socket Layer) protocol. This protocol creates and uses session keys. That is, the key is created for use in part of one session or no more than one session. It is never reused. To gain an understanding of what makes this technique so robust, I’ll give an uncomplicated description of how it works. The process most often used is called Diffie-Hellman, named after its creators. To clarify, refer to Figure 1. Alice wants to communicate securely with Bob.
(1) The secret values are shown in red.
(2) Alice picks two numbers x and y and a secret z. She uses them to calculate M and sends x ,y, and M to Bob.
(3) Bob uses x and y and chooses his own secret w. With these he calculates N.
(4) Bob sends N back to Alice.
(5) Alice uses x, z, and N to calculate the key S.
(6) Bob uses M, x and w to calculate the same key S.
The numbers used are extremely large. But modern computer power makes the computations very quickly. The magic of this process is that even though all of the numbers x, y, M, N are exchanged in the open, an attacker doesn’t know Alice’s secret z or Bob’s secret w. Without z or w, the attacker cannot compute the key.
When this single key is used, encryption is fast and efficient. That’s why it’s so popular. AV equipment establishing a secure connection will often use the Diffie-Hellman method to create a temporary session key.
Phil Hippensteel, PhD, is an instructor of information systems at Penn State Harrisburg.